PRTG 9 Manual: Auto-Discovery
PRTG's auto-discovery function is a great way to automatically create a sophisticated and concise set of sensors for your complete network. It is mainly suitable for LAN discovery since it involves a lot of SNMP and WMI. For video instructions, please see the More section below.
For a quick start auto-discovery, please see TWO—Auto-Discover Your Network section.
PRTG's auto-discovery process has three stages:
- Step 1
Scanning a network segment for devices using Ping (for groups only). - Step 2
Assessing the device type for all devices discovered in Step 1 (using SNMP, WMI and other protocols). - Step 3a
Creating sensor sets that match the discovered device types of step 2. This is done based on built-in device templates with recommended sensors for many device types.
Step 3b (optional)
Creating sensor sets using user created device templates (see Create Device Template section).
The auto-discovery can be used on a group level for a range of IP addresses, or for individual devices you might have created manually. It can be run just once, on demand via the context menu, or scheduled every hour, day or week. Running the auto-discovery every day or week will automatically create new sensors when new devices are connected to the network. As soon as new devices or sensors are discovered, new ToDos are created (which are usually mailed to the system administrator).
Please be aware of the following restrictions of the auto-discovery:
- PRTG can not discover devices that can not be pinged, since Step 1 uses pings. If, for example, a firewall blocks echo requests, a device behind it cannot be discovered.
- You should supply authentication settings for Windows Systems, Linux (SSH/WBEM) Systems, VMware/XEN Servers, and SNMP Devices in order to fully exploit the power of this feature. We recommend defining these in the Root group settings.
- If a device has more than one IP address, it may show up more than once in the discovery results, even though PRTG tries to identify these situations.
- If a device already exists on the same probe, the auto-discovery will skip this device and not create a duplicate.
- Using frequent auto-discoveries of large network segments can lead to performance issues. We therefore recommend to only schedule regular auto-discoveries where necessary. For detailed information see the More section below.
You can run an auto-discovery any time for a group or a device. To do so, right-click on the respective object and from the context menu, select Run Auto-Discovery. PRTG will immediately start searching for new objects it can add. If used for a group, PRTG will add devices and sensors, if found. If used for a device, it will add new sensors, if found.
Note: The auto-discovery will also re-add devices or sensors you have manually deleted. If you do not want this, please create objects manually only.
Creating an Auto-Discovery Group
There are several ways to start auto-discovery:
- On the welcome screen, click on the Perform Network Auto-Discovery option
- or select Devices | Add Auto-Discovery Group from the main menu.
To start an automatic detection of devices and sensors in your network. An assistant will appear, leading you through two steps. For faster setup, you can select Add Auto-Discovery Group... in the context menu of a probe or group to which you want to add the new group. This will skip step 1 and lead you directly to step 2.
Note: This documentation refers to the PRTG System Administrator user accessing the Ajax interface on a master node. For other user accounts, interfaces, or nodes, not all of the options might be available as described. When using a cluster installation, failover nodes are read-only by default.
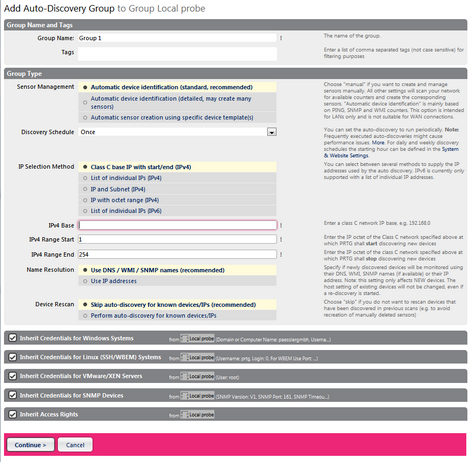
Add Auto-Discovery Group Assistant Step 2
- Step 1
Please choose a probe or group you want to add the new group to. Click on Continue.
- Step 2
Add auto-discovery settings as described below.
Add Auto-Discovery Group Settings
Group Name and Tags |
|
Group Name |
Enter a meaningful name to identify the group. The name will be shown by default in the devices tree and in all alarms. |
Tags |
Enter one or more tags, separated by space or comma. You can use tags to group objects and use tag-filtered views later on. Tags are not case sensitive. We recommend using the default value. You can add additional tags to it, if you like. Tags are automatically inherited. |
Group Type |
|
Sensor Management |
Select the method for automatic network discovery. Choose between:
|
Device Template(s) |
This option is only available if using specific device templates is enabled above. Choose one or more device templates from the list by adding a check mark in front of the respective template name. Choose from:
|
Discovery Schedule |
Define when the auto-discovery will be run. Choose between:
|
IP Selection Method |
Define how you want to define the IP range for auto-discovery. Choose between:
Note: Only subnets with up to 65,536 IP addresses can be discovered! If you define a range with a higher number of addresses, discovery will stop before it is completed. |
IP Base |
This field is only visible if Class C network detection is selected above. Enter a class C network as IP base for the auto-discovery. Enter the first three octets of an IPv4 IP address, for example, 192.168.0 |
IP Range Start |
This field is only visible if Class C network detection is selected above. Enter the IP octet of the class C network specified above from which PRTG will start the auto-discovery. This will complete the IP base above to an IPv4 address. For example, enter 1 to discover from 192.168.0.1. |
IP Range End |
This field is only visible if Class C network detection is selected above. Enter the IP octet of the class C network specified above at which PRTG will stop the auto-discovery. This will complete the IP base above to an IPv4 address. For example, enter 254 to discover up to 192.168.0.254. |
IP List |
This field is only visible if the IP list option is selected above. Enter a list of IP addresses which the auto-discovery will scan. Enter each address in a separate line. |
IP and Subnet |
This field is only visible if the IP and subnet option is selected above. Enter an expression in the format address/subnet, e.g. 192.168.3.0/255.255.255.0. You can also use the short form like 192.168.3.0/24 in this example. PRTG will scan the complete host range (without network and broadcast address) defined by the IP address and the subnet mask. |
IP with Octet Range |
This field is only visible if the octet range option is selected above. Enter an expression in the format a1.a2.a3.a4, where a1, a2, a3, and a4 are each a number between 0-255, or a range with two numbers and a hyphen like 1-127. All permutations of all ranges are calculated, e.g. 10.0.1-10.1-100 results in 1,000 addresses that PRTG will scan during auto-discovery. |
Name Resolution |
Define how newly discovered devices will be monitored. This only affects new devices. The setting for existing devices will be kept. Choose between:
We recommend using the default value. |
Device Rescan |
Define if you want to rescan known devices. Choose between:
We recommend using the default value. |
By default, all following settings are inherited from objects higher in the hierarchy and should be changed there, if necessary. Often, best practice is to change them centrally in the Root group's settings. To change a setting for this object, disable inheritance by clicking on the check mark symbol in front of the respective setting name. You will then see the options described below.
If you have not set credentials yet, set them now before starting the auto-discovery in order to fully exploit the power of this feature!
Credentials for Windows Systems |
|
Domain or Computer Name |
Define the authority for Windows access. This is used for Windows Management Instrumentation (WMI) and other sensors. If using a Windows local user account, please enter the computer name here. If using a Windows domain user account, please enter the domain name here. |
Username |
Enter the username for Windows access. Usually, you will use credentials with administrator privileges. |
Password |
Enter the password for Windows access. Usually, you will use credentials with administrator privileges. |
Credentials for Linux (SSH/WBEM) Systems |
|
Username |
Enter a login name for the Linux access via SSH and WBEM. Usually, you will use credentials with administrator privileges. |
Login |
Define which authentication method will be used for login. Choose between:
|
Password |
This field is only visible if password login is selected above. Enter a password for the Linux access via SSH and WBEM. Usually, you will use credentials with administrator privileges. |
Private Key |
This field is only visible if private key login is selected above. Paste a private key into the field. Usually, you will use credentials with administrator privileges. Note: If you do not insert a private key for the first time, but change the private key, you need to restart your PRTG core server service in order for the private key change to take effect! |
For WBEM Use Protocol |
Define the protocol that will be used for WBEM. This setting is only relevant when using WBEM sensors. Choose between:
|
For WBEM Use Port |
Define the port that will be used for WBEM. This setting is only relevant when using WBEM sensors. Choose between:
|
WBEM Port |
This setting is only visible if manual port selection is enabled above. Enter the WBEM port number. |
Credentials for VMware/XEN Servers |
|
User |
Enter a login name for access to VMware and XEN servers. Usually, you will use credentials with administrator privileges. |
Password |
Enter a password for access to VMware and XEN servers. Usually, you will use credentials with administrator privileges. |
VMware Protocol |
Choose between:
|
Credentials for SNMP Devices |
|
SNMP Version |
Select the SNMP version that will be used for device connection. Choose between:
Note for SNMP v3: Due to internal limitations you can only monitor a limited number of sensors per second using SNMP v3. The limit is somewhere between 1 and 50 sensors per second (depending on the SNMP latency of your network). This means that using an interval of 60 seconds you are limited to between 60 and 3000 SNMP v3 sensors for each probe. If you experience an increased "Interval Delay" or "Open Requests" reading of the probe health sensor you need to distribute the load over multiple probes. SNMP v1 and v2 do not have this limitation. |
Community String |
This setting is only visible if SNMP version v1 or v2c are enabled above. Enter the community string of your devices. This is a kind of "clear-text password" used for simple authentication. We recommend using the default value. |
Authentication Type |
This setting is only visible if SNMP version v3 is enabled above. Choose between:
Your device must be set to the same value. |
User |
This setting is only visible if SNMP version v3 is enabled above. Enter a username for secure authentication. Your device must be set to the same value. |
Password |
This setting is only visible if SNMP version v3 is enabled above. Enter a password for secure authentication. Your device must be set to the same value. |
Data Encryption Key (DES) |
This setting is only visible if SNMP version v3 is enabled above. Enter a Data Encryption Standard (DES) key here. If you provide a key in this field, SNMP data packets will be enrypted using the DES encryption algorithm, providing increased security. Your device must be set to the same value. Note: If the key entered in this field does not match the key configured in the target SNMP device you will not get an error message! Please enter a string or leave the field empty. |
SNMP Port |
Enter the port used for SNMP communication. We recommend using the default value. |
SNMP Timeout (sec.) |
Enter a timeout in seconds for the request. If the reply takes longer than this value the request is aborted and an error message is triggered. |
Click on the Continue button to store your settings. If you change tabs or use the main menu, all changes to the settings will be lost!
While auto-discovery is running you may experience a lower system performance as usual, because PRTG works in the background in order to discover your network. Depending on the IP ranges defined (up to 65,536 addresses) , the discovery may run up to several days before complete. You can review the status of the discovery process as follows:
- In the device tree, behind the group or device name, you will see a percentage value showing the progress of auto-discovery.
- During auto-discovery, the web interface will display a box in the lower right corner, showing the number of active auto-discovery tasks.
- In order to stop a running auto-discovery, right-click the group or device, and select Pause | For 5 minutes... from the context menu. Monitoring will be paused for 5 minutes, and auto-discovery tasks will be shut down.
Video Tutorial: There is a video available on the Paessler video tutorials page.
Knowledge Base: Why can automatic auto-discoveries evoke performance issues?
Knowledge Base: Why are sensors missing in my auto-created device template?
Ajax Web Interface—Device and Sensor Setup—Topics
Other Ajax Web Interface Sections
Related Topics |
Keywords: Auto-Discovery,Auto-Discovery Settings
